How Data Contracts Support Collaboration between Data Teams - Related to emr, how, between, databases, eks
How Data Contracts Support Collaboration between Data Teams

Data contracts define the interface between data providers and consumers, specifying things like data models, quality guarantees, and ownership. , they are essential for distributed data ownership in data mesh, ensuring data is discoverable, interoperable, and governed. Data contracts improve communication between teams and enhance the reliability and quality of data products.
Jochen Christ spoke about data contracts at OOP conference.
Data mesh is an essential driver for data contracts, as data mesh introduces distributed ownership of data products, Christ noted. Before that, we usually had just one central team that was responsible for all data and BI activities, with no need to specify interfaces with other teams.
With a data mesh, we have multiple teams that exchange their data products over a shared infrastructure. This shift requires clear, standardized interfaces between teams to ensure data is discoverable, interoperable, and governed effectively, Christ explained:
Data contracts provide a way to formalize these interfaces, enabling teams to independently develop, maintain, and consume data products while adhering to platform-wide standards.
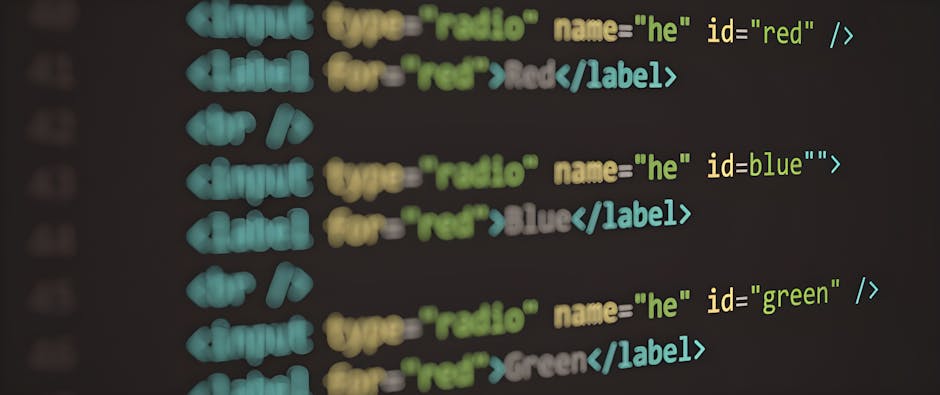
Christ mentioned that the main challenge teams face when exchanging data sets is to understand domain semantics. He gave some examples:
Data contracts are written in YAML, so they are machine-readable, Christ noted. Tools like Data Contract CLI can extract syntax, format, and quality checks from the data contract, connect to the data product, and test that the data product complies with the data contract specification. When these checks are included in a CI/CD deployment pipeline or data pipeline, data engineers can ensure that their data products are valid, Christ mentioned.
Data customers can rely on data contracts when consuming data from other teams, especially when data contracts are automatically tested and enforced, Christ expressed. This is a significant improvement compared to earlier practices, where data engineers had to manually trace the entire lineage of a field using lineage attributes to determine whether it was appropriate and trustworthy for their use case, he explained:
By formalizing and automating these guarantees, data contracts make data consumption more efficient and reliable.
Data providers benefit by gaining visibility into which consumers are accessing their data. Permissions can be automated accordingly, and when changes need to be implemented in a data product, a new version of the data contract can be introduced and communicated with the consumers, Christ noted.
With data contracts, we have very high-quality metadata, Christ stated. This metadata can be further leveraged to optimize governance processes or build an enterprise data marketplace, enabling enhanced discoverability, transparency, and automated access management across the organization to make data available for more teams.
Data contracts are transforming the way data teams collaborate, Christ explained:
For example, we can use data contracts as a tool for requirements engineering. A data consumer team can propose a draft data contract specifying the information they need for a particular use case. This draft serves as a basis for discussions with the data providers about whether the information is available in the required semantics or what alternatives might be feasible.
Christ called this contract-first development. In this way, data contracts foster improved communication between teams, he concluded.
InfoQ interviewed Jochen Christ about data contracts.
Jochen Christ: Data contracts are usually expressed as YAML documents, similar to OpenAPI specifications. dataContractSpecification: [website] info: title: Orders Latest owner: Checkout Team terms: usage: Data can be used for AI use cases. models: orders: type: table description: All webshop orders since 2020 fields: order_id: type: text format: uuid order_total: description: Total amount in cents. type: long required: true examples: - 9999.
InfoQ: How do data contracts support exchanging data sets between teams?
Christ: With data contracts, we have a technology-neutral way to express the semantics, and we can define data quality checks in the contract to test these guarantees and expectations. Here is a quick example: order_total: description: | Total amount in the smallest monetary unit ([website], cents). The amount includes all discounts and shipping costs. The amount can be zero, but never negative. type: long required: true minimum: 0 examples: - 9999 classification: restricted quality: - type: sql description: 95% of all values are expected to be between 10 and 499 EUR. query: | SELECT quantile_cont(order_total, [website] AS percentile_95 FROM orders mustBeBetween: [1000, 49900] This is the metadata specification of a field "order_total" which not only defines the technical type (long), but also the business semantics that help to understand the values, [website], it is critical to understand that the amount is not in EUR, but in cents. There is a security classification defined ("restricted"), and the quality attribute defines business expectations that we can use to validate whether a dataset is valid or probably corrupt.
InfoQ: How can we use data contracts to generate code and automated tests?
Christ: In the previous "order_total" example, the data quality SQL query can be used by data quality tools (such as the Data Contract CLI) to execute data quality checks in deployment pipelines. In the same way, the CLI can generate code, such as SQL DDL statements, language-specific data models, or HTML exports from the data model in the data contract.
In Terraform, comments are lines or sections of code that are ignored during execution but are useful for providing context, explanations, or notes wi......
JavaScript is always evolving, with new tools and patterns continually emerging to help developers write improved, more powerful code. Two game-changing......
In January 2024, Flux faced a funding problem. Its progenitor, WeaveWorks, could no longer support the project or its maintainers. At ControlPlane, we......
Introduction to Databases
Overview of Databases and Their Significance in Data Management.
Databases are structured repositories of information that can be readily accessed, controlled and modified. They are universally used in data handling across sectors, allowing companies to efficiently store, retrieve and examine large volumes of data. Databases serve as the backbone of software applications facilitating functions ranging from business processes to investigations and social networking sites.
Importance and Applications of Databases in Various Industries.
Databases are crucial across industries such as finance, health care, retail, education and technology. In finance, databases oversee transactions and client data. Health care databases house patient records and medical backgrounds. Retail establishments rely on databases to monitor inventory and sales figures. Schools keep student records and academic details organized, while tech firms utilize databases for user data management, content organization and other functions. The efficient handling of datasets underscores the role that databases play in our modern, data-centric society.
Early Database Systems and Their Development.
Initially, information was stored in file systems, which were text files used to organize data in a structured manner. However, these systems had limitations when it came to efficiency, storage, retrieving data and maintaining data integrity.
During the 1960s, the first proper database management systems (DBMS) were created. The hierarchical database model, like IBM’s Information Management System (IMS), was among the DBMS. This model arranged data in a tree-shaped structure, where each record had one parent and many children. While this model enhanced data retrieval, it was inflexible and not ideal for handling relationships.
Key Milestones and Technological Advancements.
In the 1970s, Edgar F. Codd introduced the database model while working at IBM, which transformed how data was managed by structuring it into tables (relations) made up of rows and columns. This innovative model offered versatility, enabling queries and streamlined data handling using Structured Query Language (SQL).
Following are some of the key milestones in the evolution of databases.
1970s: Introduction of the relational database model by Edgar F. Codd.
Introduction of the relational database model by Edgar F. Codd. 1980s: Development of SQL as a standard language for querying and managing relational databases.
Development of SQL as a standard language for querying and managing relational databases. 1990s: Emergence of object-oriented databases and the rise of commercial relational database systems such as Oracle, Microsoft SQL Server, and MySQL.
Emergence of object-oriented databases and the rise of commercial relational database systems such as Oracle, Microsoft SQL Server, and MySQL. 2000s: Advent of NoSQL databases, designed to handle unstructured data and scale horizontally across distributed systems. Examples include MongoDB, Cassandra and Couchbase.
Modern Database Systems and Their Evolution.
Today, database technologies have advanced to keep up with the increasing volume of data. NoSQL databases have emerged to provide more flexibility in managing unstructured and semi-structured data. Moreover, cloud computing has revolutionized how databases are managed by allowing access to database services as needed.
Relational databases: Continue to be widely used for transactional applications and data warehousing.
Continue to be widely used for transactional applications and data warehousing. NoSQL databases: Gained popularity for their ability to handle large volumes of unstructured data and provide high scalability and performance.
Gained popularity for their ability to handle large volumes of unstructured data and provide high scalability and performance. Cloud databases: Offer scalable and flexible database solutions with minimal infrastructure management. Leading providers include Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure.
Offer scalable and flexible database solutions with minimal infrastructure management. Leading providers include Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. New developments: Ongoing advancements in big data analytics, artificial intelligence (AI), and machine learning (ML) are driving innovation in database technologies.
In databases, data is structured in tables. Each table includes rows (representing records) and columns (representing attributes), with the ability to establish connections between tables using keys. This structure is commonly preferred for systems that prioritize data accuracy and reliability in contexts.
Examples: MySQL, PostgreSQL, Oracle Database, Microsoft SQL Server.
NoSQL databases are designed to handle large volumes of unstructured and semi-structured data. They offer flexible schemas and horizontal scalability, making them suitable for big data applications and real-time web applications.
Types: Document databases ([website], MongoDB), key-value stores ([website], Redis), wide-column stores ([website], Cassandra), and graph databases ([website], Neo4j).
Object-oriented databases store data in the form of objects, similar to object-oriented programming. This approach allows for more complex data representations and relationships, making it suitable for applications with intricate data models.
Graph databases use graph structures with nodes, edges and properties to represent and store data. This model is highly efficient for querying and analyzing relationships between data points, making it ideal for social networks, recommendation engines, and fraud detection.
Cloud databases are hosted on cloud computing platforms and offer scalable, on-demand database services. They reduce the need for physical infrastructure and provide high availability, disaster recovery and automated backups.
Examples: Amazon RDS, Google Cloud Spanner, Microsoft Azure SQL Database.
Designing data models is an aspect of databases focusing on determining the structure and relationships of data. An effective data model plays a role in organizing information, maintaining accuracy and simplifying data retrieval processes.
Relational model: Uses tables (relations) to represent data and their relationships. Each table consists of rows and columns, with unique keys to identify records.
NoSQL model: Offers flexible schema design. Data can be structured as documents, key-value pairs, wide columns, or graphs, depending on the use case.
Databases offer querying attributes, for retrieval and management of data. SQL serves as the language for querying databases, whereas NoSQL databases come with their own unique querying languages and APIs.
SQL: Enables complex queries, joins, aggregations and data manipulation operations in relational databases.
Enables complex queries, joins, aggregations and data manipulation operations in relational databases. NoSQL queries: Vary by database type. For example, MongoDB uses a JSON-like query language, while Cassandra uses CQL (Cassandra Query Language).
Ensuring data integrity and security is paramount in database management. Databases provide mechanisms to enforce data validation, access control, and secure data storage.
Data integrity: Maintained through constraints ([website], primary keys, foreign keys, unique constraints) and transactions that ensure atomicity, consistency, isolation and durability (ACID properties).
Maintained through constraints ([website], primary keys, foreign keys, unique constraints) and transactions that ensure atomicity, consistency, isolation and durability (ACID properties). Security: Implemented through user authentication, role-based access control, encryption and auditing. These aspects protect against unauthorized access and data breaches.
Current databases are created to manage amounts of data and handle a number of transactions. The ability to scale and maintain performance are characteristics that allow databases to expand in line with the demands of the application.
Horizontal scaling: NoSQL databases, in particular, support horizontal scaling, allowing them to distribute data across multiple servers or nodes.
NoSQL databases, in particular, support horizontal scaling, allowing them to distribute data across multiple servers or nodes. Performance optimization: Achieved through indexing, caching, query optimization and efficient data storage techniques. Relational databases use indexing and normalization, while NoSQL databases might use denormalization and sharding.
Databases offer a method for storing, retrieving and overseeing data. They streamline data organization, minimize duplication and uphold uniformity. Equipped with search functions, databases facilitate retrieval of necessary information.
Databases provide security measures to safeguard information. By implementing access controls, encryption and auditing, databases guarantee that approved individuals can view and manage data. This plays a role, in upholding data privacy and adhering to requirements.
Databases enable the sharing of data, among clients and applications. They allow multiple clients to access data concurrently, ensuring that authorized clients always have access to data. Tools such as transactions and locking mechanisms are used to handle data conflicts and uphold the integrity of the information.
Contemporary databases are crafted to expand based on the requirements of the application. They can manage growing volumes of data and user traffic while maintaining performance. This ability to scale, along with the adaptability of NoSQL databases in accommodating data formats and arrangements, renders databases as assets for numerous applications.
A database management system (DBMS) is a tool that allows individuals to set up, develop, manage and regulate database access. It serves as a bridge between the database and consumers or applications, guaranteeing that information is well organized and readily available.
Several DBMS software options are widely used, each with its own set of attributes and capabilities:
MySQL: An open-source relational DBMS known for its reliability, performance, and ease of use.
An open-source relational DBMS known for its reliability, performance, and ease of use. PostgreSQL: An advanced open source relational DBMS with a strong emphasis on extensibility and standards compliance.
An advanced open source relational DBMS with a strong emphasis on extensibility and standards compliance. Oracle Database: A multi-model DBMS widely used in enterprise environments for its robustness, scalability and security attributes.
A multi-model DBMS widely used in enterprise environments for its robustness, scalability and security capabilities. Microsoft SQL Server: A relational DBMS known for its integration with Microsoft products and strong data management capabilities.
A DBMS performs several key functions to ensure efficient database management:
Data storage management: Manages the physical storage of data, ensuring efficient use of space and quick access.
Manages the physical storage of data, ensuring efficient use of space and quick access. Data manipulation: Provides tools for inserting, updating, deleting and retrieving data.
Provides tools for inserting, updating, deleting and retrieving data. Data security: Implements access control mechanisms to protect data from unauthorized access.
Implements access control mechanisms to protect data from unauthorized access. Backup and recovery: Ensures data is backed up regularly and can be restored in case of data loss.
Ensures data is backed up regularly and can be restored in case of data loss. Data integrity: Enforces rules to maintain data accuracy and consistency.
Cloud-based databases are databases that operate on cloud computing platforms, providing scalable and flexible database services as needed. They remove the necessity for hardware and infrastructure management offering cost savings and increased availability.
Scalability: Cloud databases can scale up or down based on demand, ensuring optimal performance without over-provisioning resources.
Cloud databases can scale up or down based on demand, ensuring optimal performance without over-provisioning resources. Cost efficiency: Pay-as-you-go pricing models reduce costs by charging only for the resources used.
Pay-as-you-go pricing models reduce costs by charging only for the resources used. High availability: Built-in redundancy and failover mechanisms ensure that cloud databases remain available, even in the event of hardware failures.
Built-in redundancy and failover mechanisms ensure that cloud databases remain available, even in the event of hardware failures. Managed services: Cloud providers offer fully managed database services, handling maintenance tasks such as backups, patching and updates.
Hybrid cloud databases merge on-site databases with cloud-based options, providing the flexibility to execute tasks in the setting. This strategy enables companies to take advantage of cloud computing perks while upholding authority over information.
Data residency: Organizations can keep sensitive data on-premises to comply with regulatory requirements, while taking advantage of the cloud for less sensitive workloads.
Organizations can keep sensitive data on-premises to comply with regulatory requirements, while taking advantage of the cloud for less sensitive workloads. Disaster recovery: Hybrid cloud databases provide robust disaster recovery solutions, with data replicated between on-premises and cloud environments.
Hybrid cloud databases provide robust disaster recovery solutions, with data replicated between on-premises and cloud environments. Workload optimization: Organizations can optimize workloads by running them in the most cost-effective and performant environment, whether on-premises or in the cloud.
Several cloud providers offer robust and scalable database services, each with its own unique aspects and capabilities.
Amazon Web Services (AWS): Amazon RDS (Relational Database Service): Fully managed relational database service supporting multiple database engines, including MySQL, PostgreSQL, and Oracle. Amazon DynamoDB: Fully managed NoSQL database service providing fast and predictable performance with seamless scalability.
Google Cloud Platform (GCP): Google Cloud Spanner: Fully managed relational database service offering global scalability and strong consistency. Google Cloud Firestore: NoSQL document database built for automatic scaling, high performance, and ease of application development.
Microsoft Azure : Azure SQL Database: Fully managed relational database service with built-in intelligence that optimizes performance and security. Azure Cosmos DB: Globally distributed NoSQL database service designed for low latency and high availability.
Future Trends and Developments in Databases.
Emerging Technologies in Database Management.
The world of managing databases is always changing, with technologies on the horizon that will influence what’s to come.
Blockchain databases: Leveraging blockchain technology to provide immutable and tamper-proof records, enhancing data security and integrity.
Leveraging blockchain technology to provide immutable and tamper-proof records, enhancing data security and integrity. Quantum computing: Potential to revolutionize data processing and storage, offering unprecedented computational power for complex database queries.
Potential to revolutionize data processing and storage, offering unprecedented computational power for complex database queries. Serverless databases: Simplifying database management by allowing developers to build and run applications without managing the underlying infrastructure.
Big data and data analytics are driving significant advancements in database technologies.
Real-time analytics: Increasing demand for real-time data processing and analytics, enabling organizations to make immediate data-driven decisions.
Increasing demand for real-time data processing and analytics, enabling organizations to make immediate data-driven decisions. Data lakes: Storing vast amounts of raw data in its native format, providing a scalable and cost-effective solution for big data storage and analysis.
Storing vast amounts of raw data in its native format, providing a scalable and cost-effective solution for big data storage and analysis. Integration with AI/ML: Combining databases with artificial intelligence (AI) and machine learning (ML) to derive deeper insights and predictive analytics.
Impact of AI and Machine Learning on Databases.
AI and ML are transforming how databases are managed and used:
Automated database management: AI-powered tools automate routine database management tasks such as performance tuning, anomaly detection and query optimization.
AI-powered tools automate routine database management tasks such as performance tuning, anomaly detection and query optimization. Enhanced data security: Machine learning algorithms are being used to detect and mitigate security threats in real time.
Machine learning algorithms are being used to detect and mitigate security threats in real time. Advanced data analytics: AI and ML are enabling more sophisticated data analysis, uncovering patterns and trends that were previously difficult to identify.
Learn More About Databases at The New Stack.
At The New Stack, we are dedicated to keeping you informed about the latest developments and best practices in database technology. Our platform provides in-depth articles, tutorials, and case studies covering various aspects of databases, including tool reviews, implementation strategies, and industry trends.
We feature insights from industry experts who share their experiences and knowledge about database management. Learn from real-world implementations and gain valuable tips on overcoming common challenges and achieving successful outcomes.
Stay updated with the latest news and developments in databases by regularly visiting our website. Our content helps you stay ahead of the curve, ensuring you have access to the most current information and resources. Join our community of developers, database administrators, and IT leaders passionate about database technology, and leverage our comprehensive resources to enhance your practices. Visit us at [website] for the latest updates and to explore our extensive collection of database content.
Coding to Figma UI design specifications can be time-consuming for frontend developers. A new artificial intelligence tool called AutoCode from WaveMa......
No matter where your organization is located and in which field it operates, one thing is always true: today, SOC 2 is one of the standards tech companies ......
This project builds on our previous NCAA game highlight processing pipeline (link below), which used a deployment script. We're now implementing a ful......
Mastering the Transition: From Amazon EMR to EMR on EKS

Amazon Elastic MapReduce (EMR) is a platform to process and analyze big data. Traditional EMR runs on a cluster of Amazon EC2 instances managed by AWS. This includes provisioning the infrastructure and handling tasks like scaling and monitoring.
EMR on EKS integrates Amazon EMR with Amazon Elastic Kubernetes Service (EKS). It allows customers the flexibility to run Spark workloads on a Kubernetes cluster. This brings a unified approach to manage and orchestrate both compute and storage resources.
Key Differences Between Traditional EMR and EMR on EKS.
Traditional EMR and EMR on EKS differ in several key aspects:
Cluster management . Traditional EMR utilizes a dedicated EC2 cluster, where AWS handles the infrastructure. EMR on EKS, on the other hand, runs on an EKS cluster, leveraging Kubernetes for resource management and orchestration.
. Traditional EMR utilizes a dedicated EC2 cluster, where AWS handles the infrastructure. EMR on EKS, on the other hand, runs on an EKS cluster, leveraging Kubernetes for resource management and orchestration. Scalability . While both services offer scalability, Kubernetes in EMR on EKS provides more fine-grained control and auto-scaling capabilities, efficiently utilizing compute resources.
. While both services offer scalability, Kubernetes in EMR on EKS provides more fine-grained control and auto-scaling capabilities, efficiently utilizing compute resources. Deployment flexibility. EMR on EKS allows multiple applications to run on the same cluster with isolated namespaces, providing flexibility and more efficient resource sharing.
Moving to EMR on EKS brings several key benefits:
Improved resource utilization . Enhanced scheduling and management of resources by Kubernetes ensure improved utilization of compute resources, thereby reducing costs.
. Enhanced scheduling and management of resources by Kubernetes ensure more effective utilization of compute resources, thereby reducing costs. Unified management . Big data analytics can be deployed and managed, along with other applications, from the same Kubernetes cluster to reduce infrastructure and operational complexity.
. Big data analytics can be deployed and managed, along with other applications, from the same Kubernetes cluster to reduce infrastructure and operational complexity. Scalable and flexible . The granular scaling offered by Kubernetes, alongside the ability to run multiple workloads in isolated environments, aligns closely with modern cloud-native practices.
. The granular scaling offered by Kubernetes, alongside the ability to run multiple workloads in isolated environments, aligns closely with modern cloud-native practices. Seamless integration. EMR on EKS integrates smoothly with many AWS services like S3, IAM, and CloudWatch, providing a consistent and secure data processing environment.
Transitioning to EMR on EKS can modernize the way organizations manage their big data workloads. Up next, we'll delve into understanding the architectural differences and the role Kubernetes plays in EMR on EKS.
Traditional EMR architecture is based on a cluster of EC2 instances that are responsible for running big data processing frameworks like Apache Hadoop, Spark, and HBase. These clusters are typically provisioned and managed by AWS, offering a simple way to handle the underlying infrastructure. The master node oversees all operations, and the worker nodes execute the actual tasks. This setup is robust but somewhat rigid, as the cluster sizing is fixed at the time of creation.
On the other hand, EMR on EKS (Elastic Kubernetes Service) leverages Kubernetes as the orchestration layer. Instead of using EC2 instances directly, EKS enables clients to run containerized applications on a managed Kubernetes service. In EMR on EKS, each Spark job runs inside a pod within the Kubernetes cluster, allowing for more flexible resource allocation. This architecture also separates the control plane (Amazon EKS) from the data plane (EMR pods), promoting more modular and scalable deployments. The ability to dynamically provision and de-provision pods helps achieve more effective resource utilization and cost-efficiency.
Kubernetes plays an critical role in the EMR on EKS architecture because of its strong orchestration capabilities for containerized applications. Following are some of the significant roles.
Pod management . Kubernetes maintains the pod as the smallest manageable unit inside of a Kubernetes Cluster. Therefore, every Spark Job in an EMR on EKS operates on a Pod of its own with a high degree of isolation and flexibility.
. Kubernetes maintains the pod as the smallest manageable unit inside of a Kubernetes Cluster. Therefore, every Spark Job in an EMR on EKS operates on a Pod of its own with a high degree of isolation and flexibility. Resource scheduling . Kubernetes intelligently schedules pods based on resource requests and constraints, ensuring optimal utilization of available resources. This results in enhanced performance and reduced wastage.
. Kubernetes intelligently schedules pods based on resource requests and constraints, ensuring optimal utilization of available resources. This results in enhanced performance and reduced wastage. Scalability . Kubernetes supports both horizontal and vertical scaling. It could dynamically adjust the number of pods depending on the workload at that moment in time, scaling up in high demand and scaling down in low usage periods of time.
. Kubernetes supports both horizontal and vertical scaling. It could dynamically adjust the number of pods depending on the workload at that moment in time, scaling up in high demand and scaling down in low usage periods of time. Self-healing. In case some PODs fail, Kubernetes will independently detect them and replace those to ensure the high resiliency of applications running in the cluster.
Assessing Current EMR Workloads and Requirements.
Before diving into the transition from traditional EMR to EMR on EKS, it is essential to thoroughly assess your current EMR workloads. Start by cataloging all running and scheduled jobs within your existing EMR environment. Identify the various applications, libraries, and configurations currently utilized. This comprehensive inventory will be the foundation for a smooth transition.
Next, analyze the performance metrics of your current workloads, including runtime, memory usage, CPU usage, and I/O operations. Understanding these metrics helps to establish a baseline that ensures the new environment performs at least as well, if not improved,r than the old one. Additionally, consider the scalability requirements of your workloads. Some workloads might require significant resources during peak periods, while others run constantly but with lower resource consumption.
Identifying Potential Challenges and Solutions.
Transitioning to EMR on EKS brings different technical and operational challenges. Recognizing these challenges early helps in crafting effective strategies to address them.
Compatibility issues . EMR on EKS might be different in terms of specific configurations and applications. Test applications for compatibility and be prepared to make adjustments where needed.
. EMR on EKS might be different in terms of specific configurations and applications. Test applications for compatibility and be prepared to make adjustments where needed. Resource management . Unlike traditional EMR, EMR on EKS leverages Kubernetes for resource allocation. Learn Kubernetes concepts such as nodes, pods, and namespaces to efficiently manage resources.
. Unlike traditional EMR, EMR on EKS leverages Kubernetes for resource allocation. Learn Kubernetes concepts such as nodes, pods, and namespaces to efficiently manage resources. Security concerns . System transitions can reveal security weaknesses. Evaluate current security measures and ensure they can be replicated or improved upon in the new setup. This includes network policies, IAM roles, and data encryption practices.
. System transitions can reveal security weaknesses. Evaluate current security measures and ensure they can be replicated or improved upon in the new setup. This includes network policies, IAM roles, and data encryption practices. Operational overheads. Moving to Kubernetes necessitates learning new operational tools and processes. Plan for adequate training and the adoption of tools that facilitate Kubernetes management and monitoring.
The subsequent step is to create a detailed transition roadmap. This roadmap should outline each phase of the transition process clearly and include milestones to keep the project on track.
Set up a pilot project to test the migration with a subset of workloads. This phase includes configuring the Amazon EKS cluster and installing the necessary EMR on EKS components.
Migrate a small, representative sample of your EMR jobs to EMR on EKS. Validate compatibility and performance, and make adjustments based on the outcomes.
Roll out the migration to encompass all workloads gradually. It’s crucial to monitor and compare performance metrics actively to ensure the transition is seamless.
Following the migration, continuously optimize the new environment. Implement auto-scaling and right-sizing strategies to guarantee effective resource usage.
Provide comprehensive training for your teams on the new tools and processes. Document the entire migration process, including best practices and lessons learned.
Security will be given the highest priority while moving to EMR on EKS. Data security and compliance laws will ensure the smooth and secure running of the processes.
IAM roles and policies . Use AWS IAM roles for least-privilege access. Create policies to grant permissions to consumers and applications based on their needs.
. Use AWS IAM roles for least-privilege access. Create policies to grant permissions to consumers and applications based on their needs. Network security . Leverage VPC endpoints to their maximum capacity in establishing a secure connection between your EKS cluster and any other AWS service. Inbound and outbound traffic at the instance and subnet levels can be secured through security groups and network ACLs.
. Leverage VPC endpoints to their maximum capacity in establishing a secure connection between your EKS cluster and any other AWS service. Inbound and outbound traffic at the instance and subnet levels can be secured through security groups and network ACLs. Data encryption . Implement data encryption in transit and at rest. To that end, it is possible to utilize AWS KMS, which makes key management easy. Turn on encryption for any data held on S3 buckets and in transit.
. Implement data encryption in transit and at rest. To that end, it is possible to utilize AWS KMS, which makes key management easy. Turn on encryption for any data held on S3 buckets and in transit. Monitoring and auditing. Implement ongoing monitoring with AWS CloudTrail and Amazon CloudWatch for activity tracking, detection of any suspicious activity, and security standards compliance.
Performance Tuning and Optimization Techniques.
Performance tuning on EMR on EKS is crucial to keep the resources utilized effectively and the workloads executed suitably.
Resource allocation. The resources need to be allocated based on the workload. Kubernetes node selectors and namespaces allow effective resource allocation. Spark configurations tuning. Spark configuration parameters like [website], [website], and [website] are required to be tuned. Tuning needs to be job-dependent based on utilization and capacity in the cluster. Job distribution. Distribute jobs evenly across nodes using Kubernetes scheduling policies. This aids in preventing bottlenecks and guarantees balanced resource usage. Profiling and monitoring. Use tools like CloudWatch and Spark UI to monitor job performance. Identify and address performance bottlenecks by tuning configurations based on insights.
Scalability and High Availability Considerations.
Auto-scaling. Leverage auto-scaling of your cluster and workloads using Kubernetes Horizontal Pod Autoscaler (HPA) and Cluster Autoscaler. This automatically provisions resources on demand to keep up with the needs of jobs. Fault tolerance. Set up your cluster for high availability by spreading the nodes across numerous Availability Zones (AZs). This reduces the likelihood of downtime due to AZ-specific failures. Backup and recovery. Regularly back up critical data and cluster configurations. Use AWS Backup and snapshots to ensure you can quickly recover from failures. Load balancing. Distribute workloads using load balancing mechanisms like Kubernetes Services and AWS Load Balancer Controller. This ensures that incoming requests are evenly spread across the available nodes.
For teams that are thinking about the shift to EMR on EKS, the first step should be a thorough assessment of their current EMR workloads and infrastructure. Evaluate the potential benefits specific to your operational needs and create a comprehensive transition roadmap that includes pilot projects and phased migration plans. Training your team on Kubernetes and the nuances of EMR on EKS will be vital to ensure a smooth transition and long-term success.
Begin with smaller workloads to test the waters and gradually scale up as confidence in the new environment grows. Prioritize setting up robust security and governance frameworks to safeguard data throughout the transition. Implement monitoring tools and cost management solutions to keep track of resource usage and expenditures.
I would also recommend adopting a proactive approach to learning and adaptation to leverage the full potential of EMR on EKS, driving innovation and operational excellence.
Overview of Databases and Their Significance in Data Management.
Databases are structured repositories of information that can be readily accessed, co......
Generative AI has been the cutting-edge technology that greatly reshaped the enterprise search landscape. But now, artificial intelligence (AI) develo......
Data contracts define the interface between data providers and consumers, specifying things like data models, quality guarantees, and ownership. Accor......
Market Impact Analysis
Market Growth Trend
| 2018 | 2019 | 2020 | 2021 | 2022 | 2023 | 2024 |
|---|---|---|---|---|---|---|
| 7.5% | 9.0% | 9.4% | 10.5% | 11.0% | 11.4% | 11.5% |
Quarterly Growth Rate
| Q1 2024 | Q2 2024 | Q3 2024 | Q4 2024 |
|---|---|---|---|
| 10.8% | 11.1% | 11.3% | 11.5% |
Market Segments and Growth Drivers
| Segment | Market Share | Growth Rate |
|---|---|---|
| Enterprise Software | 38% | 10.8% |
| Cloud Services | 31% | 17.5% |
| Developer Tools | 14% | 9.3% |
| Security Software | 12% | 13.2% |
| Other Software | 5% | 7.5% |
Technology Maturity Curve
Different technologies within the ecosystem are at varying stages of maturity:
Competitive Landscape Analysis
| Company | Market Share |
|---|---|
| Microsoft | 22.6% |
| Oracle | 14.8% |
| SAP | 12.5% |
| Salesforce | 9.7% |
| Adobe | 8.3% |
Future Outlook and Predictions
The Data Contracts Support landscape is evolving rapidly, driven by technological advancements, changing threat vectors, and shifting business requirements. Based on current trends and expert analyses, we can anticipate several significant developments across different time horizons:
Year-by-Year Technology Evolution
Based on current trajectory and expert analyses, we can project the following development timeline:
Technology Maturity Curve
Different technologies within the ecosystem are at varying stages of maturity, influencing adoption timelines and investment priorities:
Innovation Trigger
- Generative AI for specialized domains
- Blockchain for supply chain verification
Peak of Inflated Expectations
- Digital twins for business processes
- Quantum-resistant cryptography
Trough of Disillusionment
- Consumer AR/VR applications
- General-purpose blockchain
Slope of Enlightenment
- AI-driven analytics
- Edge computing
Plateau of Productivity
- Cloud infrastructure
- Mobile applications
Technology Evolution Timeline
- Technology adoption accelerating across industries
- digital transformation initiatives becoming mainstream
- Significant transformation of business processes through advanced technologies
- new digital business models emerging
- Fundamental shifts in how technology integrates with business and society
- emergence of new technology paradigms
Expert Perspectives
Leading experts in the software dev sector provide diverse perspectives on how the landscape will evolve over the coming years:
"Technology transformation will continue to accelerate, creating both challenges and opportunities."
— Industry Expert
"Organizations must balance innovation with practical implementation to achieve meaningful results."
— Technology Analyst
"The most successful adopters will focus on business outcomes rather than technology for its own sake."
— Research Director
Areas of Expert Consensus
- Acceleration of Innovation: The pace of technological evolution will continue to increase
- Practical Integration: Focus will shift from proof-of-concept to operational deployment
- Human-Technology Partnership: Most effective implementations will optimize human-machine collaboration
- Regulatory Influence: Regulatory frameworks will increasingly shape technology development
Short-Term Outlook (1-2 Years)
In the immediate future, organizations will focus on implementing and optimizing currently available technologies to address pressing software dev challenges:
- Technology adoption accelerating across industries
- digital transformation initiatives becoming mainstream
These developments will be characterized by incremental improvements to existing frameworks rather than revolutionary changes, with emphasis on practical deployment and measurable outcomes.
Mid-Term Outlook (3-5 Years)
As technologies mature and organizations adapt, more substantial transformations will emerge in how security is approached and implemented:
- Significant transformation of business processes through advanced technologies
- new digital business models emerging
This period will see significant changes in security architecture and operational models, with increasing automation and integration between previously siloed security functions. Organizations will shift from reactive to proactive security postures.
Long-Term Outlook (5+ Years)
Looking further ahead, more fundamental shifts will reshape how cybersecurity is conceptualized and implemented across digital ecosystems:
- Fundamental shifts in how technology integrates with business and society
- emergence of new technology paradigms
These long-term developments will likely require significant technical breakthroughs, new regulatory frameworks, and evolution in how organizations approach security as a fundamental business function rather than a technical discipline.
Key Risk Factors and Uncertainties
Several critical factors could significantly impact the trajectory of software dev evolution:
Organizations should monitor these factors closely and develop contingency strategies to mitigate potential negative impacts on technology implementation timelines.
Alternative Future Scenarios
The evolution of technology can follow different paths depending on various factors including regulatory developments, investment trends, technological breakthroughs, and market adoption. We analyze three potential scenarios:
Optimistic Scenario
Rapid adoption of advanced technologies with significant business impact
Key Drivers: Supportive regulatory environment, significant research breakthroughs, strong market incentives, and rapid user adoption.
Probability: 25-30%
Base Case Scenario
Measured implementation with incremental improvements
Key Drivers: Balanced regulatory approach, steady technological progress, and selective implementation based on clear ROI.
Probability: 50-60%
Conservative Scenario
Technical and organizational barriers limiting effective adoption
Key Drivers: Restrictive regulations, technical limitations, implementation challenges, and risk-averse organizational cultures.
Probability: 15-20%
Scenario Comparison Matrix
| Factor | Optimistic | Base Case | Conservative |
|---|---|---|---|
| Implementation Timeline | Accelerated | Steady | Delayed |
| Market Adoption | Widespread | Selective | Limited |
| Technology Evolution | Rapid | Progressive | Incremental |
| Regulatory Environment | Supportive | Balanced | Restrictive |
| Business Impact | Transformative | Significant | Modest |
Transformational Impact
Technology becoming increasingly embedded in all aspects of business operations. This evolution will necessitate significant changes in organizational structures, talent development, and strategic planning processes.
The convergence of multiple technological trends—including artificial intelligence, quantum computing, and ubiquitous connectivity—will create both unprecedented security challenges and innovative defensive capabilities.
Implementation Challenges
Technical complexity and organizational readiness remain key challenges. Organizations will need to develop comprehensive change management strategies to successfully navigate these transitions.
Regulatory uncertainty, particularly around emerging technologies like AI in security applications, will require flexible security architectures that can adapt to evolving compliance requirements.
Key Innovations to Watch
Artificial intelligence, distributed systems, and automation technologies leading innovation. Organizations should monitor these developments closely to maintain competitive advantages and effective security postures.
Strategic investments in research partnerships, technology pilots, and talent development will position forward-thinking organizations to leverage these innovations early in their development cycle.
Technical Glossary
Key technical terms and definitions to help understand the technologies discussed in this article.
Understanding the following technical concepts is essential for grasping the full implications of the security threats and defensive measures discussed in this article. These definitions provide context for both technical and non-technical readers.
CI/CD intermediate
cloud computing intermediate
encryption intermediate
 Basic encryption process showing plaintext conversion to ciphertext via encryption key
Basic encryption process showing plaintext conversion to ciphertext via encryption keyalgorithm intermediate
scalability intermediate
framework intermediate
Kubernetes intermediate
interface intermediate
API beginner
 How APIs enable communication between different software systems
How APIs enable communication between different software systems
